ven the creator of MINIX operating system didn’t know that his for-education operating system is on almost every Intel-powered computer. He is okay with Intel using his creation but said in an open letter that he would have preferred if the company would have told him, just as a courtesy.
The OS was living on the Intel Management Engine chip without the knowledge of anyone. Afterall, who would want to tell everyone about it when the chip can be used to take complete control of a machine without the knowledge of the user, the primary OS, or any antivirus installed.
It was in September when Positive Technologies revealed that they found a way to unplug the power cable from Intel’s ME. The God-Mode tech, present in the Program Controller Hub, is largely undocumented and has restricted access.
The security firm Postive Technologies earlier promised to tell more about the God-Mode in December at Black Hat Europe and said that they had found a way for “an attacker of the machine to run unsigned code in the Platform Controller Hub on any motherboard.”
For now, Positive has dropped more details about the super-secretive chip in the form of a couple of tweets.
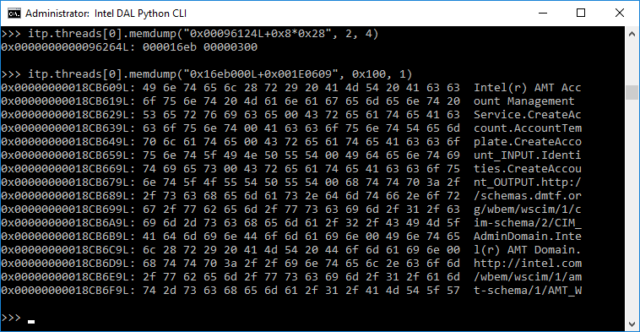
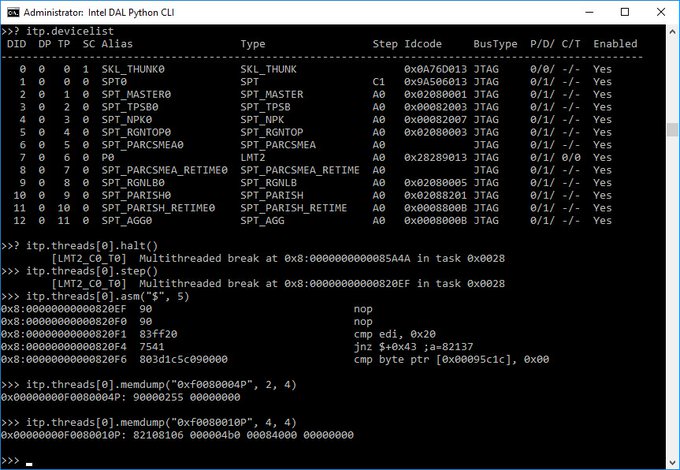
It is now known that the recent version of Intel ME chip supports the JTAG (Joint Test Action Group) debugging ports, which can be accessed over USB ports. JTAG provides low-level access to Intel CPUs, mostly used for the purpose of fixing problems. This could allow people to dig deeper into the ME chip in search for vulnerabilities.
Since the release of Intel Skylake CPUs, the Platform Controller Hub provides ME chip access to the USB ports through an interface called DCI (Direct Connect Interface), explained the Russian-language post linked in the tweet.
If an attacker is trying to compromise the chip using vulnerabilities other than the remote ones, if they exist, it would require physical access to the target machine.


No comments:
Post a Comment