Do you use a computer nowadays? The answer could be yes because that might be the machine you’re using to read this post. So, without doing any useless talk, let’s come to the point. What is the reason you think our computers or any other hardware run into problems? It could be one or many.
Other than the obvious and inevitable ones like aging, unexpected power surge, hardware failure, people not taking good care of their computer can be a topic of utmost concern. It can reduce the life expectancy of your machine and make it slower by the day.
Why your computer hates you? Why is it so slow?
So, if you’re among the careless ones and do one or many things mentioned below, your slow computer would most likely hate you if it were a person.
1. You deprive your PC of software updates and security patches
If you want to know the answer to the question “Why is my computer so slow?”, Chances are high you may find it on the software update screen. You might realize that tons of software updates and bug fixes are pending.
Software updates are important; your vendor might have done changes and updates to improve the machine’s overall performance.
So, not letting your computer update regularly would deprive it of new features, as well as, security patches for the latest bugs discovered now and then. And you should also keep the virus definitions of your antivirus software up to date.
The same goes for other software you’re using on your computer. Problems related to a particular app can affect the overall performance of your system.
2. You don’t care if there is dust and filth are all over your computer
I can recall days in college, my roommate’s computer had layers of dust deposit, and he didn’t even take the pain to wipe it once in months.
If you want to prevent your computer from dying a premature death, keep in mind, dust and electronics don’t go along, ever. It shouldn’t be a thing that you have to wash your hands after using your computer.
Dust deposit also occurs inside a computer around the cooling fan, thus, trapping the outbound heat from the components within the body itself. Eventually, the internal hardware wears out faster than it should, and it is a reason for a slow computer over time. So, you need to keep your computer neat and tidy if you want it to last for a few years. Don’t forget to read our article on
how to prevent your computer from overheating.
3. You don’t think before downloading stuff
Don’t be that person who just fills their computer with things he doesn’t even know what they do or if they’re needed. It’s also the case that people don’t pay attention while downloading or installing software and end up getting adware and other freebies.
These free tools can be bad for your computer and might open gates for malware invasion. That’s how ransomware sneaks into people’s computer. Becuase they click any random link and the rest happens in the background. Consider using some
anti ransomware tools if you think some ransomware might land on your computer.
4. You’ve stored digital garbage on your hard drive
Now, filling your hard drive with data won’t cost anything to you nor me. It’s your hard drive, and you can do whatever you want. But doing the same on a regular basis might upset your computer, especially, if most of the data is absolute garbage. Like, the photos of your childhood crush that are still lying in that hidden folder, or the videos in the study folder you have already watched.
In the case of Windows, features like System Restore and Hibernate require some space on your hard drive to store related data. Moreover, keeping unnecessary things on your hard drive increases work for the
antivirus software and the
defragger, as they have to handle more files while scanning.
Filling the hard drive up to the brim can have its disadvantages. Your PC needs some space vacant to work efficiently. The recommended amount of free space you should leave is between 10 to 15%, if you can manage more, it would be better.
5. You load tons of programs during startup
Another answer to “Why is my computer so slow?” is that you allow too many applications to load on startup. Not to mention, most of them are installed by the OEM. Your PC will definitely hate you if you’re lazy enough to disable the unnecessary ones.
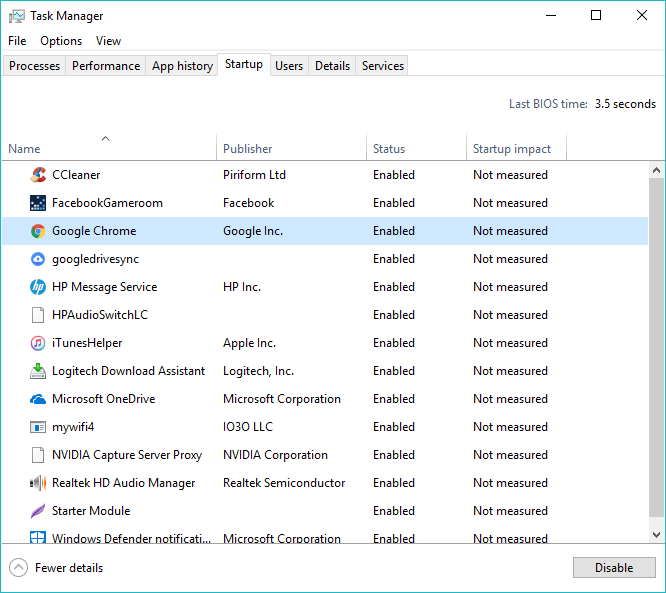
Slow computer fix: disable startup programs
In Microsoft Windows 10, you can disable startup program by visiting Task Manager > Startup. Click the desired application in the list and click Disable. Similarly, you can prevent apps from loading at startup on your other operating systems like MacOS, and Linux distros. Similarly, you can read various other tips and tricks to
make your Windows PC faster and improve performance.
6. You never shutdown or restart your computer
Many people are often confused if they should keep their PC running forever, properly Shutdown after every use, or at least, Restart it once in a while. You can clear your confusion by reading our detailed post on
whether you should restart your PC or not.
A system restart clears your computer’s RAM and shuts down all the processes. It helps the system get a fresh start after incidents of freezing or software crash, and solve problems like RAM leakage, or broken installations. So, use this slow computer fix and reduce your worries.
7. You never fix issues on your computer
Now, some apps or malware has been messing around with your system for a while, and you don’t seem to care much because all you believe is Netflix and chill, and Facebook. As a response, your angry computer slows down to the level that one day you can’t use it. Then you’ll be left with two choices: fix what’s broken or get a new machine.
You shouldn’t forget the hardware part. A faulty RAM chip or a hard drive going rogue can cause problems for your computer. It would make the computer lag and crash more often. So, consider replacing malfunctioning hardware as soon as possible.
8. You connect to unknown WiFi networks
Everything that’s labeled “free” isn’t always good. Things are similar in case of WiFi. If you find
open WiFi networks at public cafes, airports, parks, don’t immediately rush to connect to the network and soak some internet out of it. And here I am not talking about the WiFi networks other than ones authorities have deployed as a part of customer service.
The free WiFi network could be bait set up by some attacker trying to get access to people’s computer using
different WiFi hacking apps to steal information and install malicious stuff including ransomware.
Moreover, you should turn off the Bluetooth radio on your computer. It’s also equally vulnerable as tons of attack vectors take advantage of Bluetooth.
9. Your computer’s security isn’t tight enough
10. You’re running your daddy’s operating system
Even though I still have a soft corner for Windows XP, I won’t prefer the deceased veteran over Windows 10. Apart from the feature updates offered by the new versions, new operating system versions also enhance the security by fixing bugs discovered in the past. And since the new OS versions are the part of their developers’ mainstream support, new bugs are fixed first for them.
The story is similar in the case of other operating systems, be it the macOS or some Linux distribution. Even your beloved old OS would want you to be a part of the evolution and switch to a newer version.
So, these were some reason I think might slow down your computer, and your digital friend might stop loving you if you don’t change your habits. If you have something to add, you can drop your suggestion in the comments.