ow do you safeguard your computer from malicious stuff, by using an antivirus software? But what if the protector of your digital friend can’t be trusted?
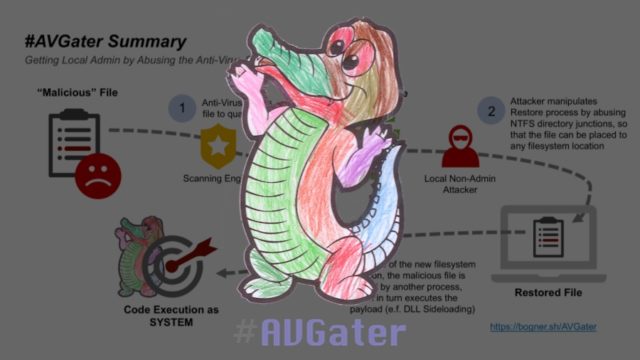
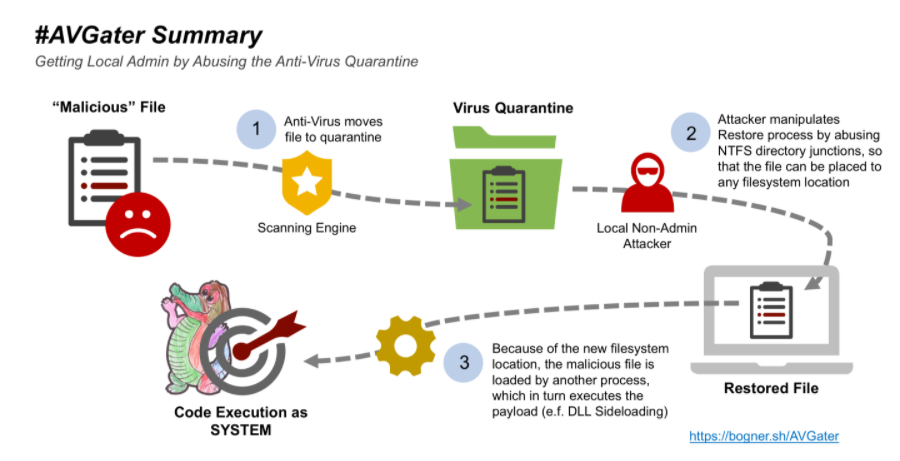
A new exploit called AVGator is created by an Austra-based security consultant named Florian Bogner. Many AV software provide functionality to quarantine files, but the users can restore the quarantined files whenever they want.
Using AVGator to mishandle the ‘restore from quarantine’ feature can allow a local user to gain full control of a computer. In normal cases, a user without admin privileges can’t perform write operations in “C:\Program Files or C:\Windows folders.
AVGator allows the users to do so by abusing a Windows NTFS directory junctions. Thus, a user can restore quarantined malicious files to a new location, even sensitive ones such as the Program Files folder, and infect the system.
However, there is one major downside associated with the attack which reduces its scope to a great extent. It can only be performed by a user having physical access to a target machine. So, you can set aside your thoughts of abandoning your antivirus software. Afterall, they are all we have got to keep bad things out from our machines. But always keep your antivirus software updated to prevent it from any unknown threats.
Bogner informed various antivirus vendors whose products could be compromised using the AVGator exploit. Some of the manufacturers have already released a fix including Trend Micro, Emsisoft, Kaspersky, Malwarebytes, Zonealarm, and Ikarus.

No comments:
Post a Comment