arlier this week, a new, widescale ransomware campaign was spotted by security solution firms. Named Bad Rabbit, this malware is spreading as a disguised Adobe Flash Player installer. After the installation, the files are encrypted and the victim is asked to pay the ransom.
As per Cisco Talos, Bad Rabbit appears to be based on DoublePulsar backdoor-based Nyetya malware, which is based on the popular Petya ransomware. As per the findings, the major portions of Rabbit’s code have also been rewritten.
The early reports suggested that there wasn’t any use of NSA-developed exploits in this attack. However, Talso suggests that Bad Rabbit uses an exploit named EternalRomance to bypass security over SMB file-sharing connections. The said exploit was published in the ShadowBrokers leak. It’s worth noting that Microsoft has patched the said exploit in March.
The EternalRomance implementation overwrites a kernel’s session security context and enables an attacker to launch remote services. It also allows the arbitrary data read/write into kernel memory.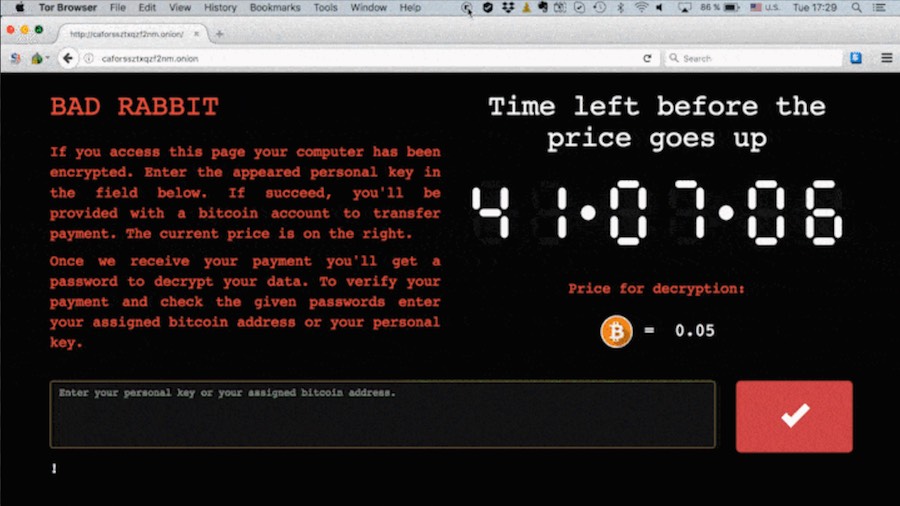

It has also been found out that the build toolchain for Bad Rabbit is very similar to Nyetya’s. Also, the evasion techniques in Nyetya and Bad Rabbit also share a similar and advanced level of understandings of the exploits used.
It’s worth noting that notorious WannaCry ransomware was the first malware attack that used NSA’s EternalBlue exploit. It was followed by NotPetya ransomware that used EternalBlue and EternalRomance exploits.
You can read the detailed finding by Cisco Talos in their blog post.
Did you find this update on Bad Rabbit ransomware helpful? Don’t forget to share your views with us.


No comments:
Post a Comment